Currently, cybercriminals are trying to infect companies in Latin America with malware by sending fake resumes that contain a remote access Trojan.
ESET shares examples of this practice and presents some to take into account to identify these scams and thus keep systems protected.
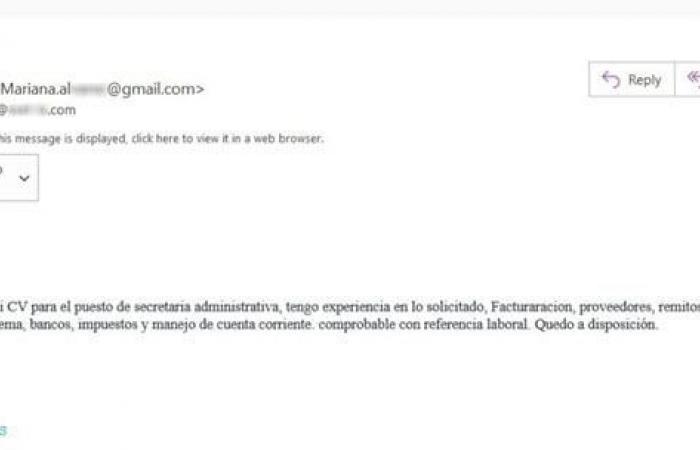
The company shares some of the examples of resumes with malware that are sent to different companies in the region:
Caption: The malicious file is shared in .zip format.
Caption: Another example of an apocryphal resume containing malware.
At first glance, these emails appear legitimate, in fact the email address in both cases does not seem to be false, and the writing does not present spelling or grammar errors that could cause alarm. Even so, according to ESET, there are always small details that allow us to detect when an email may be distributing malicious content.
“In the case of the email supposedly sent by Mariana Alvarez, it is striking that the email is not addressed to any person in particular (something that is repeated in the example of Catalina Muñoz). And, furthermore, the name is not included in the greeting. But the most striking thing, in both examples, is that the attached file is in .zip format, and its weight,” comments Camilo Gutiérrez Amaya, head of the company’s Research Laboratory in Latin America.
If the false resume is downloaded, the user will be infected with malware and thus giving the cyber attacker the possibility of obtaining sensitive information linked to their email access credentials, home banking, credit cards; access confidential company information.
Additionally, you may be allowed to install unauthorized software to commit other types of crimes, such as encrypting files or blocking access to systems throughout the organization.
“To mitigate the risk of being a victim of this type of attack, it is important to systematize good practices, and as an organization or company it is also relevant to take action on the matter by protecting the systems as well as providing training to its collaborators to detect phishing attempts. “adds the ESET Latin America researcher.
When you receive an email – especially if it is unexpected – there are several details and signs that can indicate a phishing attempt. Before clicking, the company team recommends checking two details:
-
The writing and spelling in the subject and content of the message. Although thanks to Artificial Intelligence, cyberattackers manage to write increasingly coherent and elaborate messages, it is always good to read them thoroughly and verify that there are no errors that raise suspicion.
-
The file extension—whether it is .jpg, pdf, or similar—must at least match the document that the email claims to attach. As we see in the examples of this campaign, the supposed resumes are actually .zip files (a compressed file).
As for extra protection, it is essential for detection to have a robust and reliable security solution that can provide protection against this and other types of malware attacks.