Santiago, June 24, 2024.- Password leaks are becoming more and more common. This year a report looked at “the mother of all breaches,” the leak of data stolen during a series of attacks on several companies and online services, including LinkedIn and Twitter (now X) that reportedly included 26 billion records. packed with sensitive information, such as government data and access credentials.
This number of compromised records is in addition to previous known leaks such as the Cam4 data leak that exposed nearly 11 billion records, or the so-called Collection No.1, which exposed 773 million login names and passwords previously stolen from various organizations.
This context helps understand that even with strict personal security measures in place, an account’s credentials can still get caught up in different collections, primarily due to breaches at large enterprises.
Some options to find out if your credentials have been compromised, recommended by ESET, are:
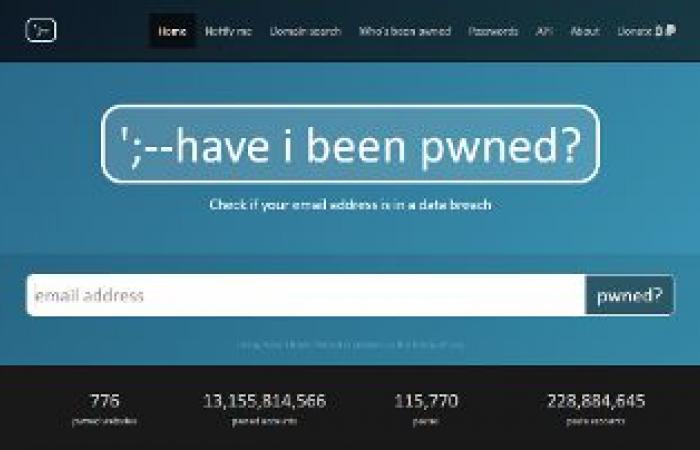
Haveibeenpwned.com: This site has a free tool that can tell you when and where your data, such as email address or passwords, appeared. Just enter your email address, click “pwned?” and a message will appear informing you of the security status of your credentials, as well as the exact leak in which they were involved. For the lucky ones, the result will be green, indicating that there has been no “pwnage,” and for the less fortunate, the site will turn red, indicating which data breach or breaches your credentials appeared in.
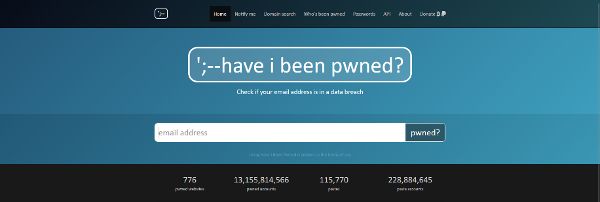
Checking emails and passwords on haveibeenpwned.com using a simple search query
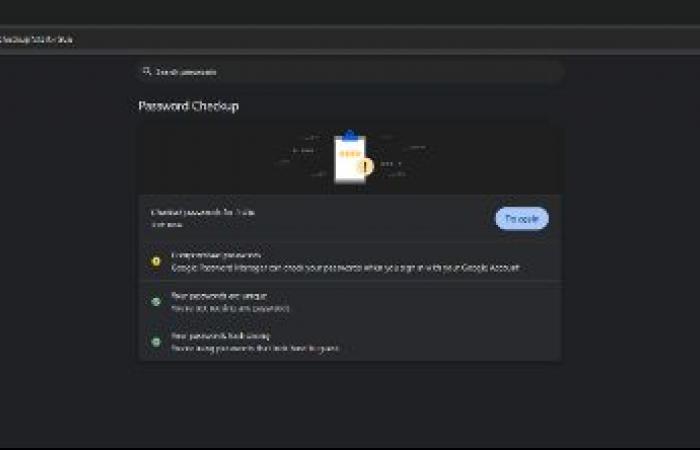
Web navigator: Some web browsers, such as Google Chrome and Firefox, can check to see if your passwords have been included in a known data breach. Chrome may also recommend stronger passwords through its password management module or offer other features to improve the security of your passwords.
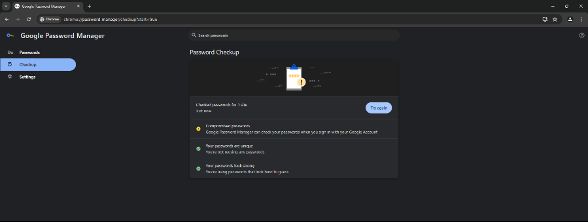
Chrome’s password manager can be very useful for finding out if your data has been publicly leaked
However, you may want to go further and use a dedicated password manager that has a proven track record, including using strong encryption. These tools typically include reputable multi-layered security software.