A few days ago, Microsoft announced that it will finally opt for “deprecate” NTLM. Although this may seem like a drastic change in the position of Windows and its well-known backward compatibility, the truth is that it was “a death foretold”. This change was foreseeable, and both Microsoft as its employees have been stating since October 2023 through different media.
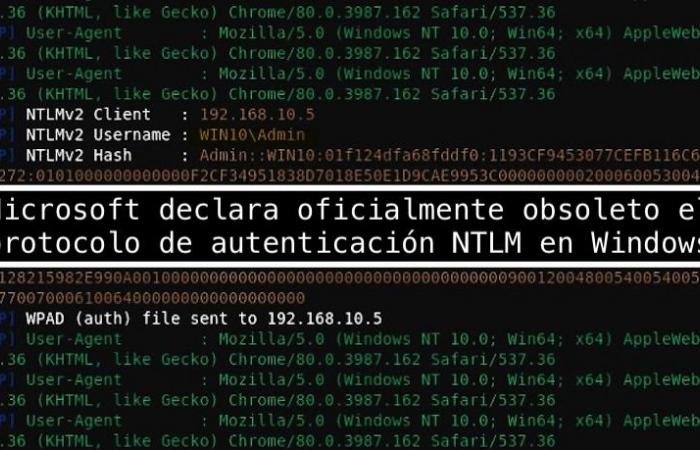
Figure 1: Microsoft officially declares the protocol obsolete
NTLM authentication on Windows
You already know that NTLMhad a predecessor (and also a few successors or alternatives), you will all know L.M. either LAN Manager. This protocol that was born in 1987 when MicrosoftWith IBMdeveloped a network operating system, the so-called OS/2. It didn’t take long for the world to show the inherent vulnerabilities of the algorithm. LM hash.
To create these hasheswe start with the first of the restrictions, passwords of a maximum of 14 characters. Then, despite allowing both upper and lower case, all letters were converted to upper case, so the character set was halved, and passwords like “Hacker” either “hacker” generated the same hash.

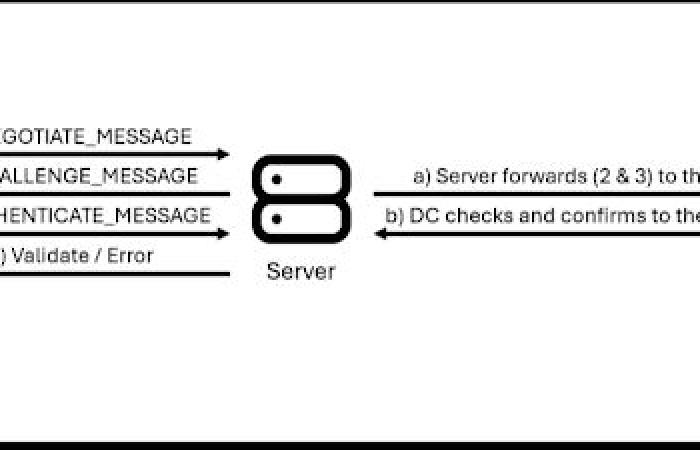
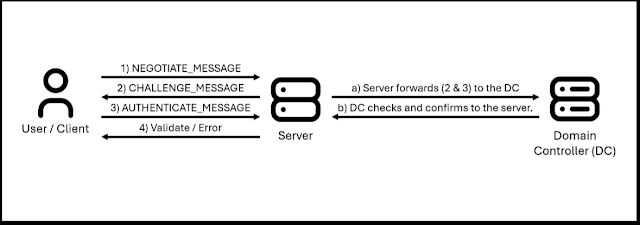
Microsoft I had to do something, and it was born NTLM (New Technology LAN Manager), the successor authentication protocol of LAN Manager. This protocol, which first appeared in 1993 next to Windows NT 3.1, uses a challenge-response mechanism to authenticate a client to a server using a password. The operating flow of NTLM is the following:
1) The client begins a negotiation with a server and sends a NEGOTIATE_MESSAGE announcing its capabilities and supported security features.
2) Once the details of the communication have been negotiated (for example, the version of LDAP to use), the server responds with a CHALLENGE_MESSAGE, which includes a nonce (a random number) that the client will have to encrypt with the hash of its password (which must be equal to the NTLM hash stored in the SAM). This nonce is 8 bytes in NTLMv1 and 16 bytes in NTLMv2.
3) After this, the client responds with an AUTHENTICATE_MESSAGE, which contains the nonce encrypted with the NT hash of the user’s password, along with other authentication data.
- In the case of an Active Directory environment, the server sends the challenge and the response sent by the client to the domain controller for verification.
- The domain controller verifies the response and sends the authentication confirmation to the server.
4) Finally, if the verification sent by the domain controller is correct, the server will either successfully validate the user or, conversely, return an error.
As you can see, in this authentication process NTLM At no time has the user’s password been used directly, but rather it is used to create his or her NTLM hash, hash which is stored in the SAM (Security Account Manager) of the team. Due to the absence of “salting” and that NTLM hash and the password are equivalent to the secret level in the protocol NTLM, the well-known PassTheHash attack makes sense. In this type of attack, an attacker who has obtained the NTLM hash of a user can authenticate as that user without needing to know their plain text password.

Finally, comment on the definitive successor of NTLM, Kerberosan authentication protocol created by the M.I.T. in 1989open source and maintained by a large community, among which is Microsoft which develops its own version (largely compatible with the “official“).
Kerberosleaves behind the challenge-response method of the authentication protocol NTLM and starts using a ticket system to authenticate users. In Kerberos we find key components such as the key distribution center (KDC), the authentication server (ACE), the concession server tickets (TGS), … All this can be seen in more detail in another post.

Figure 7: Kerberos.org Mission
The mission of Kerberos is to establish itself as the universal authentication platform in all networks in the world, as they say kerberos.org. At the moment, Kerberos is the default primary authentication protocol, while NTLM intervenes in specific circumstances. For example, it is used NTLM when authenticating across systems configured in a workgroup rather than a domain, in local authentication on controllers that are not part of a domain, or in applications that do not support other types of protocols.
You yourself can use a Fiddler (a proxy that records all traffic HTTP/HTTPS between the team and Internet) to collect all the requests made, and by observing the headers, detect in which cases it is being used Kerberos either NTLM. In an authorization header, if the token begins with “YII“we will be facing a case where it is being used Kerberos. If, on the other hand, it begins with “TLR“we will be faced with an authentication protocol different from Kerberos (usually NTLM). For example:
- Kerberos authentication header:
- Authorization: Negotiate YIIVDAYGKwYBE…
- Non-Kerberos authentication header:
- Authorization: Negotiate TlRMTVNTUA…
Returning to the news, with this announcement, Microsoft has committed to working to eliminate and mitigate all of these scenarios that make use of NTLM in components of Windows, and when they see fit they will disable it completely. This movement has caused a wave of reactions among users. Some praise this change, others wonder why now and not ago twenty years, and others defend the use of NTLMcriticizing the lack of backward compatibility that this modification will imply for older equipment.
Now it’s time to wait and see how Microsoft keep moving until we see the complete elimination of NTLM. However, it is a positive change since we go from using an authentication protocol where knowledge of the hash of the user completely breaks security; to use by default a more secure protocol such as Kerberos. And for Ethical Hacking, get your act together with Pass-the-ticket.
Greetings,