ESET explains how to know if your data has been exposed and what to do to reduce its impact.
Password breaches are becoming more common, so ESET, a leading proactive threat detection company, explains how to find out if your keys have been compromised and shares some tips to reduce the impact of a data breach that has exposed your passwords. credentials.
This year a report looked at “the mother of all breaches,” the leak of data stolen during a series of attacks on several companies and online services, including LinkedIn and Twitter (now X) that reportedly included 26 billion records. packed with sensitive information, such as government data and access credentials. This number of compromised records is in addition to previous known leaks such as the Cam4 data leak that exposed nearly 11 billion records, or the so-called Collection No.1, which exposed 773 million login names and passwords previously stolen from various organizations.
This context helps understand that even with strict personal security measures in place, an account’s credentials can still get caught up in different collections, primarily due to breaches at large enterprises.
Some options to find out if your credentials have been compromised, recommended by ESET, are:
Haveibeenpwned.com: This site has a free tool that can tell you when and where your data, such as email address or passwords, appeared. Just enter your email address, click “pwned?” and a message will appear informing you of the security status of your credentials, as well as the exact leak in which they were involved. For the lucky ones, the result will be green, indicating that there has been no “pwnage,” and for the less fortunate, the site will turn red, indicating which data breach or breaches your credentials appeared in.
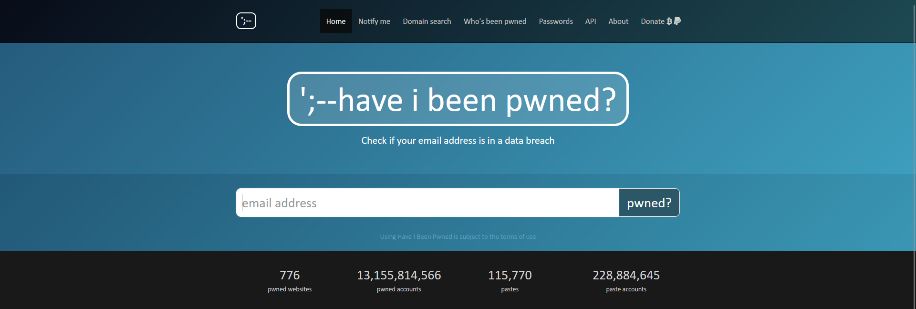
Image caption: Checking emails and passwords on haveibeenpwned.com using a simple search query
Web navigator: Some web browsers, such as Google Chrome and Firefox, can check to see if your passwords have been included in a known data breach. Chrome may also recommend stronger passwords through its password management module or offer other features to improve the security of your passwords.
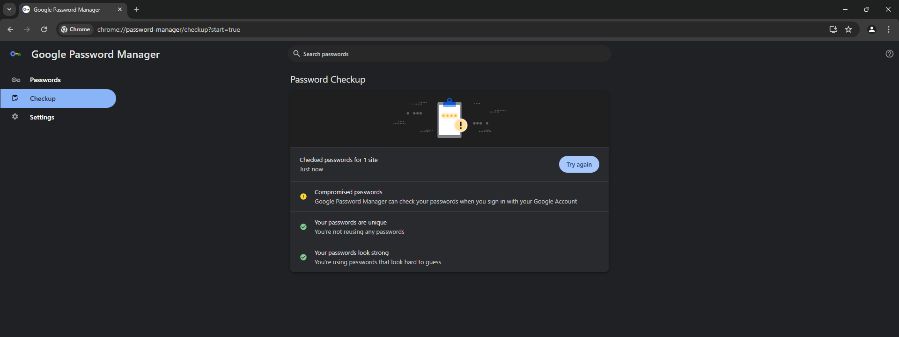
Caption: Chrome’s password manager can be very useful for finding out if your data has been publicly leaked
However, you may want to go further and use a dedicated password manager that has a proven track record, including using strong encryption. These tools typically include reputable multi-layered security software.
“Password managers are invaluable when it comes to juggling a large collection of login credentials, as they can store them securely and generate complex, unique passwords for each of your online accounts. It goes without saying, however, that you need to use a strong but memorable master password containing the same. While they are not immune to attacks, advantages such as checking leaked passwords and integration with two-factor authentication (2FA) systems currently available on many online platforms, offset the risks”, comments Camilo Gutiérrez Amaya, Head of the ESET Latin America Research Laboratory.
Likewise, to avoid the impact of credential leaks from ESET they recommend:
- Don’t rely solely on passwords. Use two-factor authentication (2FA) on all services that allow it, ideally in the form of a dedicated 2FA security key or an authenticator app such as Microsoft Authenticator or Google Authenticator. This will make it much more difficult for attackers to gain unauthorized access to accounts, even if they have somehow obtained the password(s).
- Avoid making passwords simple and short, such as a word and a number. A good practice is to use passphrases, which can be more secure and easier to remember. If in doubt, you can use this ESET tool to generate passwords, or check the strength of existing ones.
- Regarding the security of passwords as such, avoid writing access data on paper or storing them in a note-taking application. It’s also best to avoid storing account credentials in web browsers, which often save them as simple text files, making them vulnerable to data exfiltration by malware.
For companies, ESET advises taking the following points into account:
- Proactively reduce your attack surface and react as soon as something suspicious is detected. Vulnerability management is crucial, as being aware of software loopholes helps prevent their exploitation by cybercriminals.
- Implement a data loss prevention (DLP) solution and implement a robust backup policy. Additionally, handling large volumes of customer and employee data requires strict encryption practices. Local credential encryption can safeguard this sensitive data, making it difficult for attackers to exploit stolen information without access to the corresponding encryption keys.
“Ultimately, there is no one-size-fits-all solution, and each user or business must tailor their data security strategy to their specific needs and adapt to the evolving threat landscape. However, a combination of cybersecurity best practices will go a long way toward preventing data leaks and breaches,” concludes Gutiérrez Amaya from ESET Latin America.
To learn more about computer security, visit the ESET news portal: https://www.welivesecurity.com/en/privacy/password-leaks-how-to-check-affected/
On the other hand, ESET invites you to learn Secure Connection, your podcast to find out what is happening in the world of computer security. To listen to it go to: https://open.spotify.com/show/0Q32tisjNy7eCYwUNHphcw
Visit us in:
![]() @ESETLA
@ESETLA ![]() /compay/eset-latinoamerica
/compay/eset-latinoamerica ![]() /esetla
/esetla ![]() /ESETLA
/ESETLA ![]() /@esetla
/@esetla
About ESET
ESET® provides cutting-edge digital security to prevent attacks before they happen. By combining the power of AI and human expertise, ESET® stays ahead of known and emerging cyber threats, securing businesses, critical infrastructure, and individuals. Whether it’s endpoint, cloud or mobile protection, their native AI and cloud-based solutions and services are highly effective and easy to use. ESET technology includes strong detection and response, ultra-secure encryption, and multi-factor authentication. With 24/7 real-time defense and strong local support, it keeps users safe and businesses running uninterrupted. An ever-evolving digital landscape demands a progressive approach to security: ESET® is committed to world-class research and powerful threat intelligence, backed by R&D centers and a strong global partner network. For more information, visit https://www.eset.com/latam or follow us on LinkedIn, Facebook and Twitter.
Communication and Press Contact Information
María Fernanda Hernández González [email protected]
Alejandro Trincado [email protected]
Martín Gutierrez [email protected]
Tahiana Gonzalez [email protected]
For more information you can get in touch through [email protected] or at +54 11 2150-3700.
Copyright © 1992 – 2024. All rights reserved. ESET and NOD32 are registered trademarks of ESET. Other names and brands are trademarks of their respective companies.